Security Investigation Tool in Google Workspace
The security investigation tool identifies, assesses, and takes action on the security issues in the domain. Super administrators can use the Google Workspace premium edition. Other Google Workspace basic editions can use the Audit and Investigation page in the admin console. Administrator uses the investigation tool for a subset of data sources with Cloud Identity Premium, Frontline Standard, Enterprise Standard, and Education Standard. Let’s see the use of the security investigation tool, supporting editions, Common use, audit, and investigation page here.
Uses of the Security Investigation Tool
The security investigation tool used to Access data about devices, Device log data to get a clear view of the devices and applications being used to access your data, Gmail messages, including email content, Gmail log data to find and erase malicious emails, mark emails as spam or phishing, or send emails to user inboxes, View search results that list suspended users, Access Drive log data to investigate file sharing in your organization, investigate the creation and deletion of documents, investigate who accessed document and more.

Supporting editions for the Security Investigation Tool
The following editions support the Security Investigation Tool
- Enterprise Plus
- Education Standard
- Education Plus and
- Enterprise Essentials Plus

Admins can also use the investigation tool for a subset of data sources with
- Cloud Identity Premium,
- Frontline Standard,
- Enterprise Standard, and
- Education Standard
The Security Investigation Tool does not work for specific data sources. So, use the Audit and Investigation page.
The most common uses of the investigation tool
The common usage of the security investigation tool is listed here. Take action based on search results and search and investigate user log events. Investigate malicious emails and a user across data sources. The investigation tool ends meetings and views sensitive message content. Transfer a Drive file from an unknown owner and Investigate Chat messages to moderate content and protect your data.
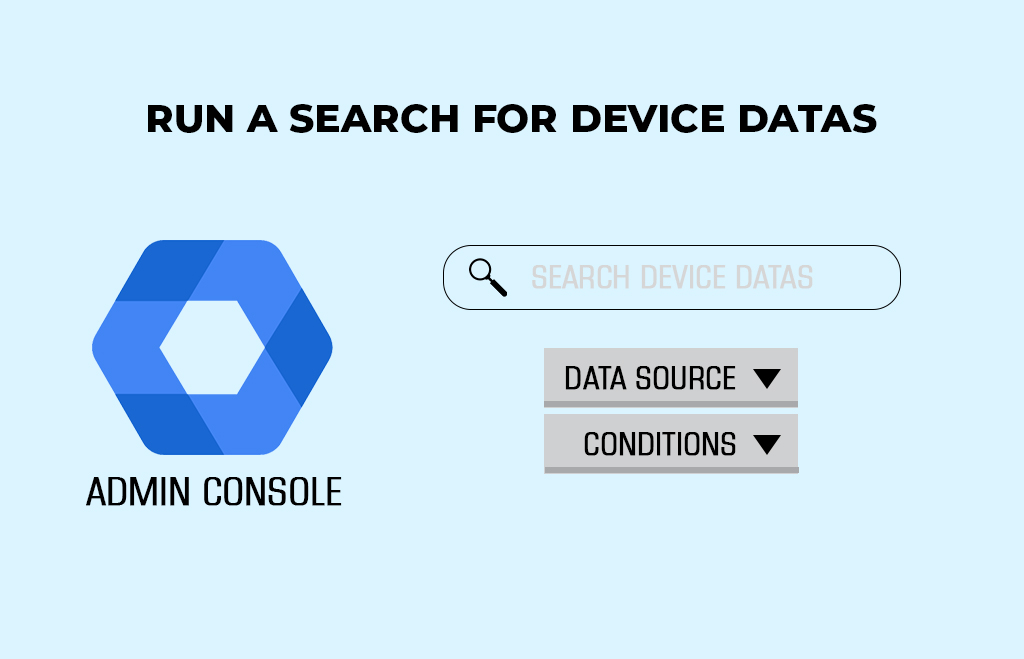
Run a search for device datas
As an administrator, you can use the security investigation tool to view and investigate live-state data about devices in your organization. Investigate whether a browser update has reached all devices in your organization. Find out if any devices are currently compromised, learn the date of a device’s last operating system update, and see the device status.
To run a search in the investigation tool,
- First, choose a data source.
- Choose one or more conditions for your search.
Steps to search for device data
- Go to Admin console Home page,
- Click Security > Security Center> Investigation tool.
- Hit Data Source and select Devices.
- Click Add Condition.
- Go to Attribute > Select an option.
- Click Contains > Select an operator.
- Enter a value, or select a value from the drop-down list.
- To add more search conditions, repeat steps 4–7.
- Click Search.
- To save your investigation, click Save > enter a title and description > click Save.
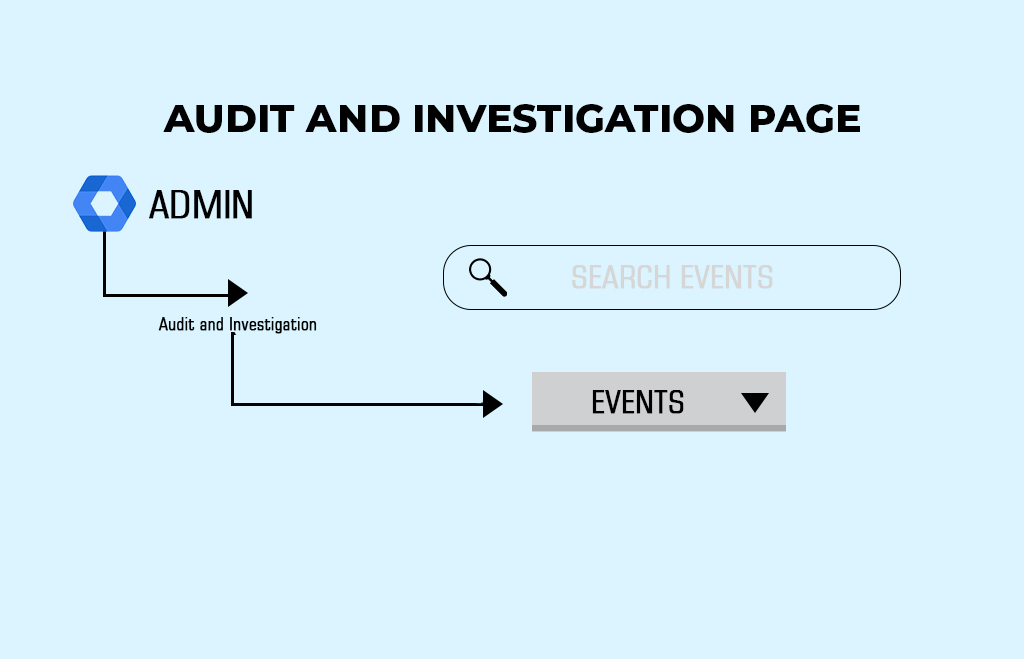
Audit and investigation page
Non-premium Google Workspace edition users (Business Starter, Business Standard, Business Plus, Education Fundamentals, Education Standard, Enterprise Essentials, or Enterprise Standard) can view log event data by accessing the basic features of the audit and investigation page.
Non-Premium Google Workspace Edition users can do the following
- Run searches with multiple filters
- Use And, Or operators
- Download search results (maximum of 100,000 rows per download)
- Create reporting rules
You can access the audit and investigation page from the left navigation menu.
- Reporting.
- Audit and Investigation.
Admins can control the security-related aspects of user accounts in Google Workspace. Based on the investigation admin takes action related to the user, device, and account.
Navohosting offer many services to our clients like
- Google workspace
- Domain & hosting
- Web design
How to setup endpoint verification on computer?
Steps to Install Google Workspace Marketplace app?
Setup New Google Workspace Email Routing Settings
Check our page to learn about our services here.


2 Responses